In this article, we will talk about Account Password Policies and how we configure them domain wide with a more granular approach of per-user password policies without using Group Policy.
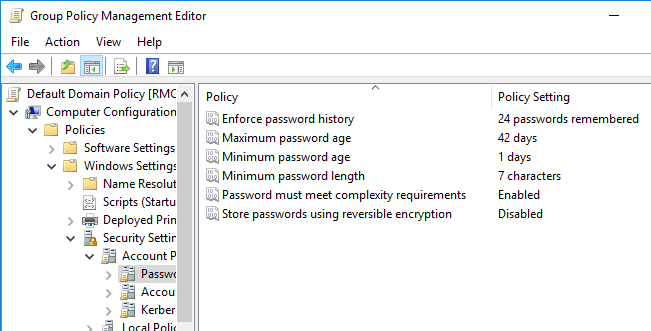
So first off, let us talk about Group Policy configuration for password complexity and requirements.
The downside of group policy settings is that it is not very granular; it is applied to OU containers and computer objects.
To change the account policies using Group Policy, go to any domain controller in your organization, open Group Policy Management Console (gpmc.msc), go to Security Settings, then Account Policies and then Password Policies.
But as I said before these settings apply to computer objects and thus ares not very granular. We don’t want to make organizational wide changes for just one user that maybe wants a weaker password and somehow managed to get an approval from the CISO of the organization.
Configuring Fine-Grained Password Policies in AD
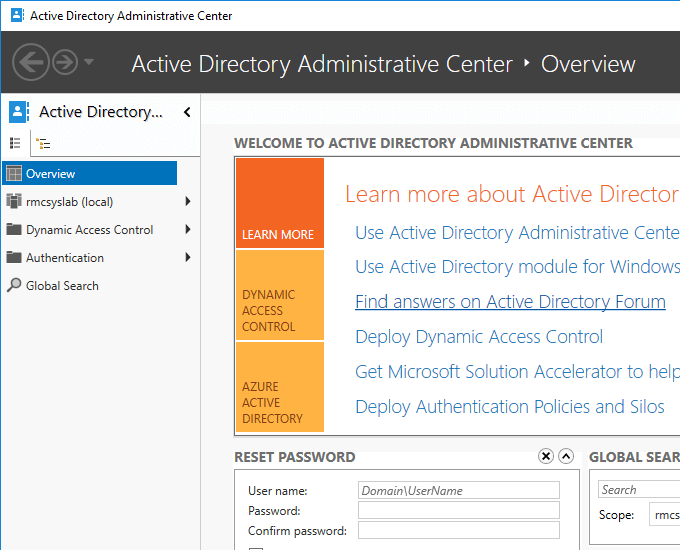
For this scenario, we will use the Active Directory Administrative Center situated in Server Manager under Tools.
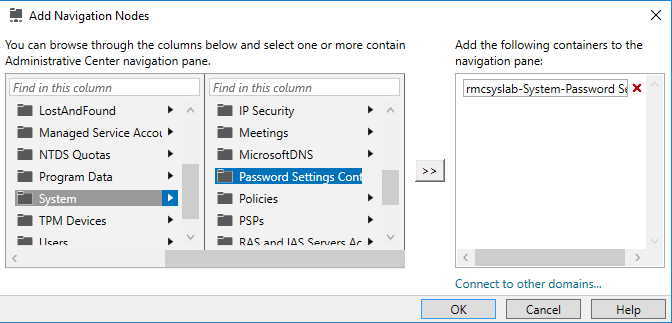
Before we dive into the actual PSO (Password Setting Object) configuration, we must first add another node to manage in the console.
Right click in the empty area below Global Search and choose Add Navigation Nodes.
Then navigate to System, Password Settings Container and then click Add.
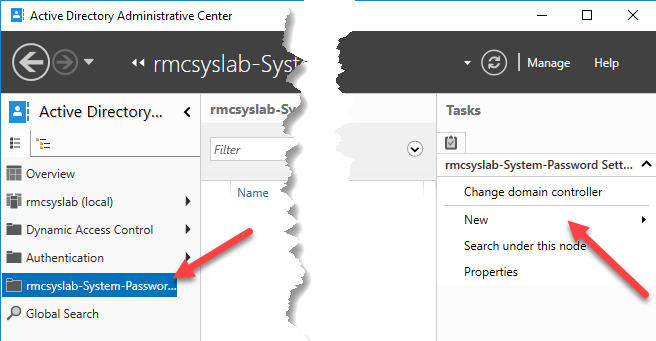
Back to the Administrative Center, you will see a new management node has been added. Click on it and then go to New, Password Settings.
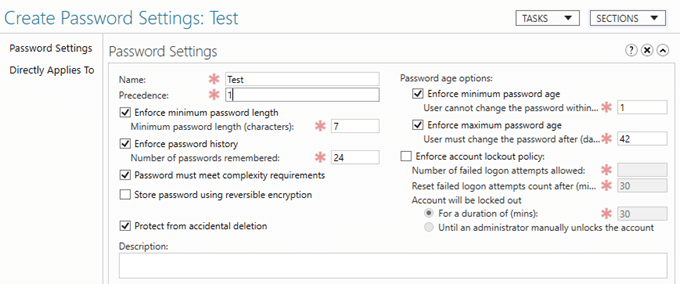
You will then be greeted with the following Create Password Settings screen.
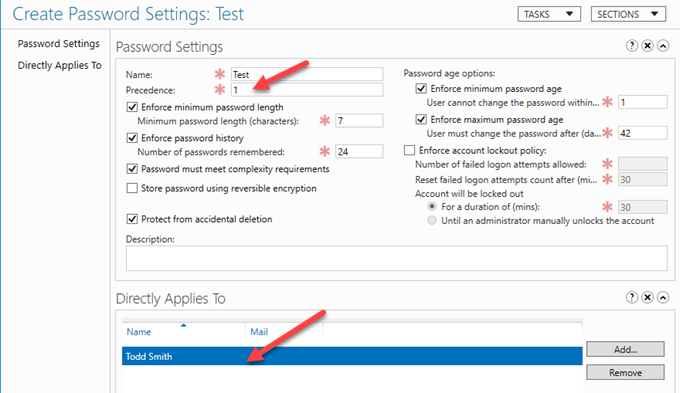
For test purposes, we will leave all the values at their default values, give a name to the PSO (Test), and then choose whom we want to apply this PSO to.
So after going to Add, and choosing the user Todd Smith, I can see that this PSO is applied and only applied to this user, regardless of OU location, GPO and so forth. Don’t forget to set the Precedence value to 1, which is the highest value that takes precedence over all other settings.
That is it! Very simple and very cool. This way we can assign certain password policies to users without building complicated GPOs, OU structures and so forth. Enjoy!