Hello and welcome to a new article on fixing stuff that’s not supposed to break in the first place!
This time we are looking at a very old issue, since the dawn of sysadmin time as we know it: the issue where our domain member server or computer loses its trust relationship to the domain.
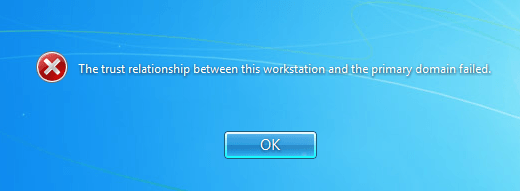
Yes, yes, the dreaded words that appear on your login screen once you try to login to one of your servers on a very sunny and rather hot Monday, after a good and quiet weekend.
The trust relationship between this workstation and the primary domain failed.
Well, a lot of us would just go in with the local administrator account and just rejoin the machine to the domain. But here are some other alternatives, including what to do if we don’t remember the local administrator password and we only have the domain login. Luckily, there’ a way to bypass that annoying issue.
Firstly, we never need to rejoin the machine to the domain if we have this problem. Run the following command from an administrator command prompt or PowerShell prompt:
Netdom resetpwd /Server:<your-domain-controller> /UserD:<domain-admin-account> /PasswordD:<domain-admin-password>
Now to dissect the command: we call the netdom command with the resetpwd (reset password) switch and we provide the domain controller we will authenticate against, and the credentials of a domain admin account. Simple. I will also explain in a little bit why this issue actually happens in the first place.
We can also use PowerShell to achieve the same goal.
Reset-ComputerMachinePassword -Server <your-domain-controller> -Credential (Get-Credential)
So easy! We don’t even have to restart the machine after these commands!
Forgot Local Admin Password
Now what do we do if we don’t remember the local administrator password?
Again, the solution is simple. We just take out the network cable, then restart the server or computer with the network cable unplugged and then login using our domain account that we used to login before.
Since the Operating System will “see” that there is no network connection, it will use its cache to authenticate you, which means it won’t even try to query the domain controllers.
Once you’re in, just plug the network cable back and you are free to try the commands we talked about above.
Why This Error Occurs
Now I promised an explanation on why this issue actually happens. Well, since I promised, here we go.
Every computer account, when joined to the domain, originally has a password, a machine password that’s used by schannel (secure channel) to authenticate the machine with the domain.
This password also has an expiration date, same as your regular user account, where you’re asked to change your password, in this case the machine negotiates a new password with the domain, and the new password is updated in both places.
So, if you ever get this error, either the server or computer was turned off for a very long time, the machine password passed its expiration date, and the machine was not online to renew it, thus the domain does not trust this machine.
Or someone by accident, or even you (yes you), deleted the computer account in AD, recreated it, and didn’t run the commands we talked about earlier after you recreated the computer account.
Well that’s enough from me, I hope you enjoyed this article, and looking forward to having you back for more. Until then… rm -rf /! (No, don’t try that actually).