Have you ever wondered what is happening under the hood when connecting to a Windows share? There is one easy way to find out. Use a packet sniffer such as Wireshark.
What is Wireshark?
Wireshark is a simple to install and easy to use packet capturing tool that is supported on both Windows and Linux. On Windows, Wireshark utilizes the Windows Pcap module as its underlying engine to capture packets. Wireshark is layered on top of Pcap to provide an easy to utilize interface and packet filter.
The easiest way to monitor packets between two machines is simply to install Wireshark on one of the two machines and then set up a filter to view the traffic. In this example, we will be monitoring the traffic between a Windows 10 client machine and a Windows 2012 server.
Setting up a File Share
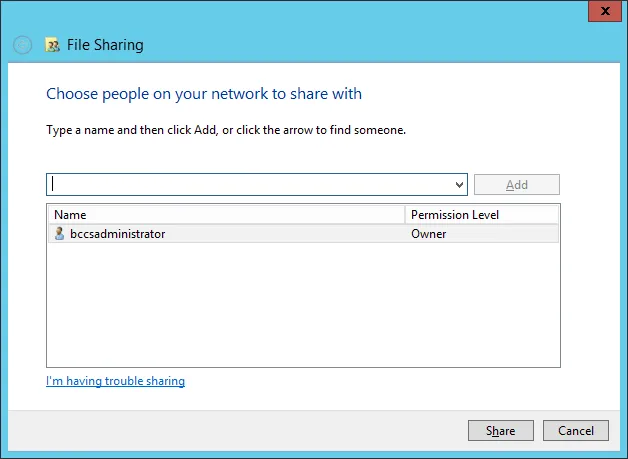
First, we will set up a share on the Windows 2012 machine. On the Windows 2012 machine, create a new folder and name it “share“. Right click and select Properties. Go to the Sharing tab and choose Share. Allow the administrative user to access the share with read and write privileges. In this case, the administrator is already the owner of the share.
Confirm your share is listening with the net share command.
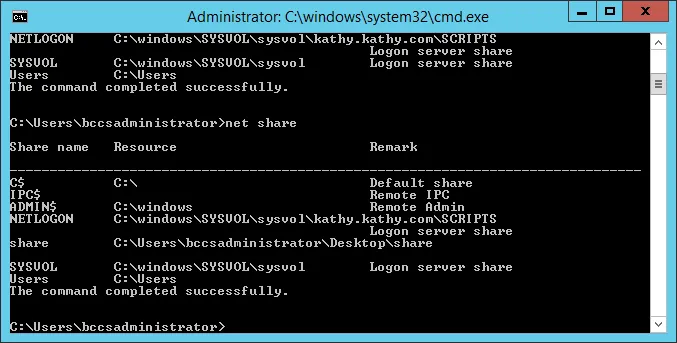
Setting up the Client
Next, on the Windows 10 machine, we will connect to our newly created network share with the command line.
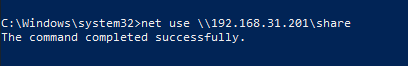
Once share connectivity is confirmed, it is time to see what is going on. Let’s install Wireshark on the Windows 10 machine. Wireshark is available for download from www.wireshark.org. In this example we will be using Wireshark-win64-2.6.6.exe. Simply hit next and choose all the defaults in the Wizard to install.
When running Wireshark, the first step is always to start a capture on a designated interface. In the Wireshark menu, go to Capture | Options. Choose the desired interface on which to listen and start the capture. In this case, we only have one network adapter to choose from.
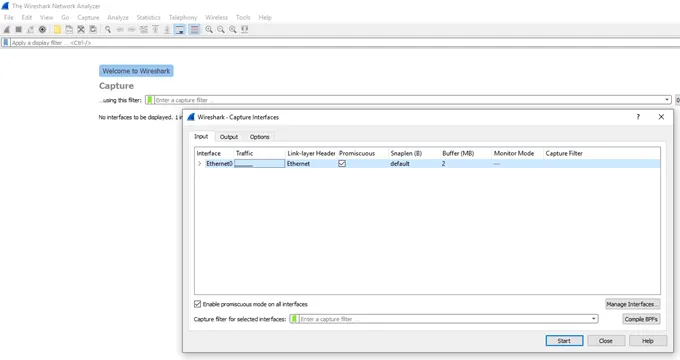
Once listening, you will see all the traffic on the interface.
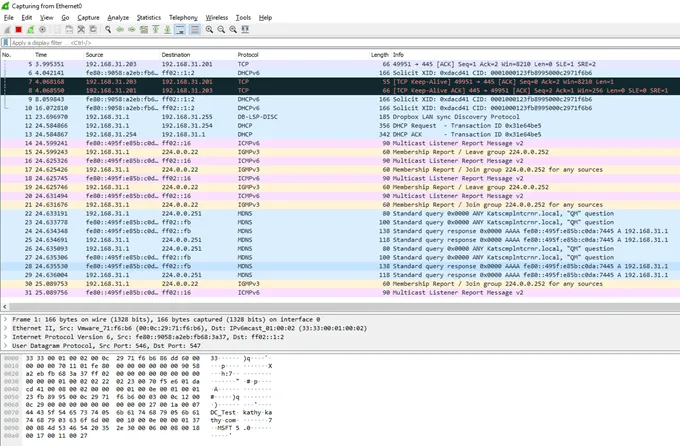
Filtering the Traffic
To see only the traffic involved in the SMB exchange, we will need to set up some filters. If you don’t know all the filter commands, Wireshark has a handy GUI that can be used to set up filters. In the top pane next to the search bar, choose Expression. This will bring up the “Wireshark – Display Filter Expression” window.
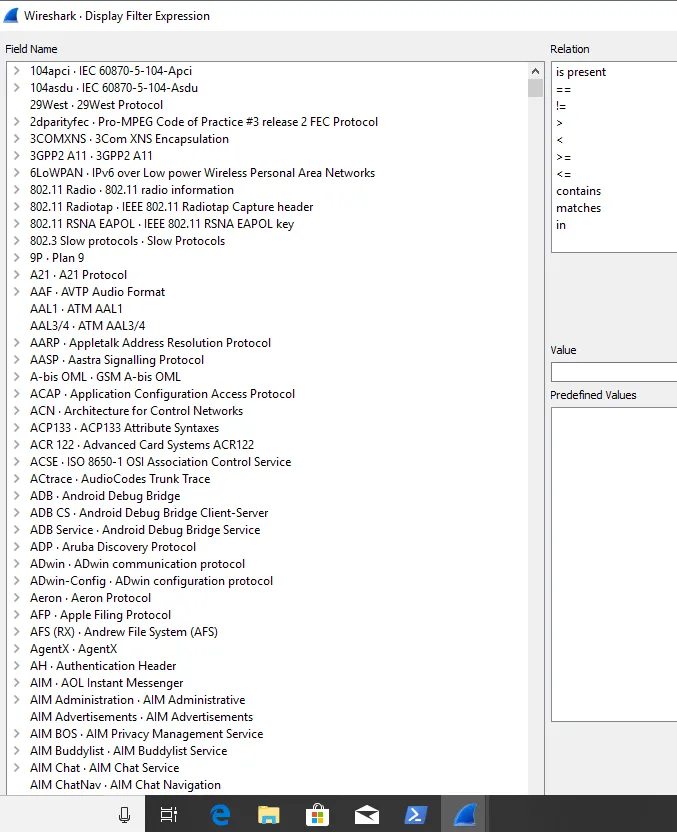
From this window, navigate by protocol to find the appropriate filter. In this case, the simplest introductory filter to narrow down our traffic is to limit the traffic by IPv4 address.
We will go to the IPv4 address and set ip.addr == 192.168.31.201 which is the IP address of the SMB share. This same command can simply be typed directly in to the search bar if you are more advanced Wireshark user. Now, traffic is limited only to traffic between our client and the Windows 2012 server.
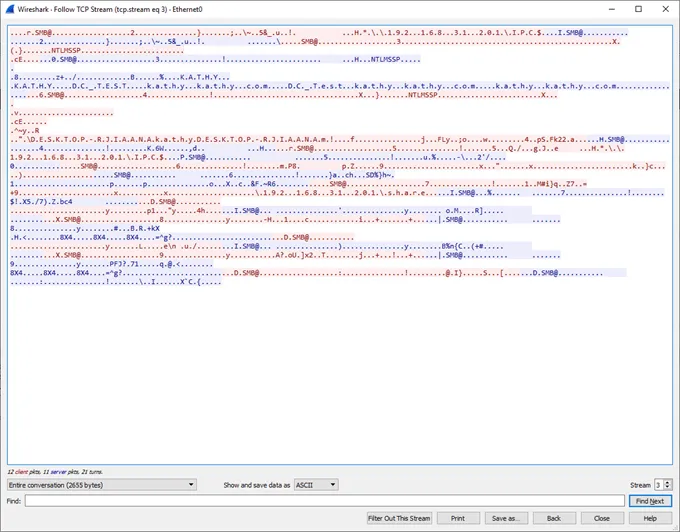
Let’s see if we can get some more information out of this capture. First, we will delete the share. On the Windows 10, run the command prompt as an administrator and type net use \\192.168.31.201\share delete. Below is an example of the TCP stream during the delete. A little more information is provided in clear text this time.
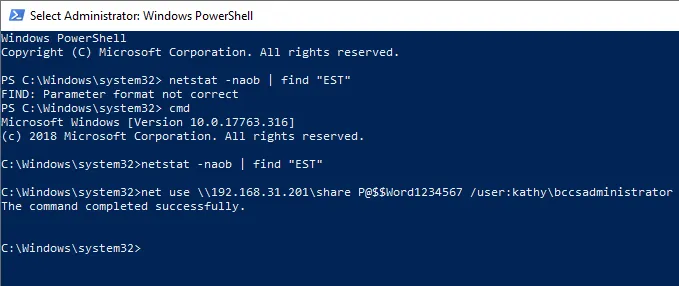
Next, we will restart the entire connection from the beginning to make sure our credentials are protected. First, confirm there is no established session by running netstat and filtering for any ESTABLISHED sessions. Then, connect back to the share with explicit credentials and then Follow TCP Stream.
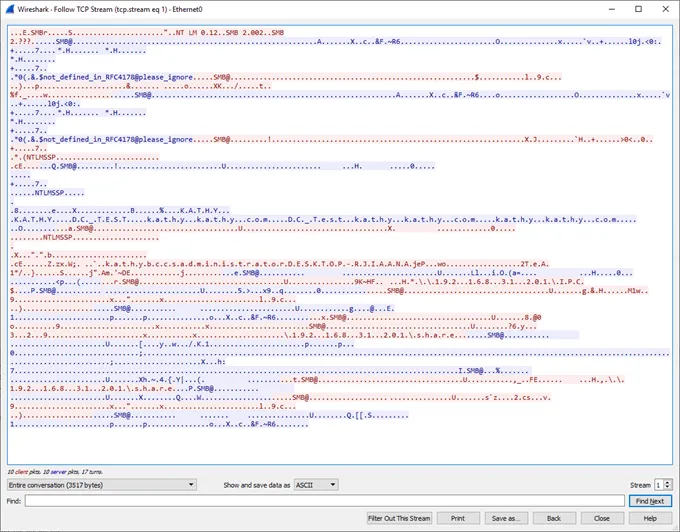
Hooray! No clear text passwords. However, I do see a username. It might be time to upgrade to SMBv3.
This simple example demonstrates how to utilize Wireshark to monitor network connections. Wireshark can be utilized to sniff all network traffic to either troubleshoot connections or to determine whether packet exchanges have clear text that should be further protected. Wireshark is one more tool to add to your security arsenal. Happy sniffing!