I have just patched some of my Windows Server 2016 servers with the new May 2018 KB, which fixes a CredSSP vulnerability, but at the same time creates an issue when trying to RDP from a non-patched system.
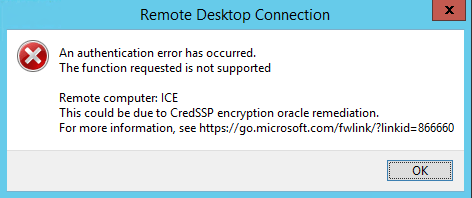
After I finished my workday, one of the project managers sent me a message saying RDP is broken and that he cannot RDP to one of the production servers. Immediately, I went back to my workstation, tried to RDP and was presented with a very strange error message as shown below:
I went to to the provided link and learned that Microsoft released a security patch that affects the RDP mechanism. Specifically, the CVE-2018-0886 update.
A remote code execution vulnerability exists in the CredSSP protocol. The attacker would need to run a MITM (Man-in-the-middle) application attack against the RDP session, which would then give him the open door to install software, change user accounts, view or change data and so forth.
Therefore, it is great that Microsoft fixed this issue, but how do we fix the above RDP error? After some digging, I found the two KBs that Microsoft released.
http://www.catalog.update.microsoft.com/Search.aspx?q=KB4093120
https://www.catalog.update.microsoft.com/Search.aspx?q=KB4103715
These two KBs relate to Windows Server 2012 R2 and 2016 along with Windows 8.1 and 10 (1607).
So after installing the KB on Windows Server 2016, Server 2012 R2 systems and the client computers, the issue was fixed immediately. Please keep in mind you need to restart the systems after the update is finished, so it is ideal to plan the update at nighttime.
An interesting issue with a rather quick fix, which was not too easy to find. If you Google CVE-2018-0886, you will find a range of resources and documentation on this issue and KB articles for other systems older than 2012 R2. Enjoy!