Most data uploaded to the cloud is protected by the standard username and password authentication, and is usually stored in plaintext for easy access and retrieval.
However, because some data can be sensitive and confidential, this level of protection will not be enough against certain threats or to meet certain requirements such as :

- External intruders – If intruders somehow get a hold of your login credentials, they can gain unauthorized access to your data.
- Insider threats – malicious insiders from within the datacenter, which may come in the form of a disgruntled network engineer or technician, can pose a serious threat to your data.
- Data protection/security laws and regulations like HIPAA, PCI DSS, and EU GDPR – companies handling sensitive customer data are required by certain laws to enforce added security and protection. Hence, storing data in plaintext won’t suffice.
To mitigate the risks brought about by these situations, you need to employ data encryption.
What Is Encryption?

Simply put, encryption is the process of disarranging or scrambling data by using an encryption key. That ‘scrambled data’ will then be stored in the server. Encrypted data can be completely useless to an intruder even if that person is able to gain unauthorized access to it.
When a legitimate user retrieves the data for use, a decryption key is used to rearrange (decrypt) the data from the server back to its usable state. There are many types of encryption, but when you talk about encryption in the cloud, they’re generally grouped into two types – client-side encryption and server-side encryption.
Client-Side Encryption

This is when both the encryption key and decryption key are created and stored on the user side, and the data is encrypted prior to being uploaded to the server.
In other words, once the data is received by the server for storage, it will already be in encrypted form. This is a very effective method of encryption, as the key (at the client side) and encrypted data (at the server side) are stored in different locations. Access to either key or data alone is useless.
The drawback of this method is that it requires the user to remember or store the decryption key. When that key is lost or forgotten, the encrypted data associated with it will be rendered useless – even to the legitimate owner.
Server-Side Encryption

This is when the encryption/decryption keys are created at the server side, in the cloud.
Upon upload, the server will perform data encryption itself with only the cloud platform knowing which key is associated to the corresponding encrypted data through its own algorithm and processes. This type of encryption is automatically done in the cloud and does not require memorization or storage of any key by the user.
Amazon S3 or Amazon Simple Storage Service is one cloud service that offers this type of encryption. If you have sensitive data that needs to be encrypted, Amazon S3 can meet your needs.
Below are the steps and processes you need to carry out if you want to encrypt your data via the web-based GUI provided by Amazon S3.
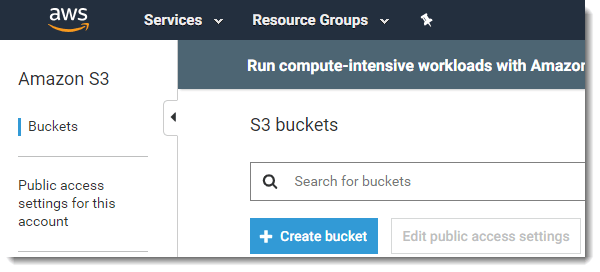
- Login to your Amazon AWS account, activate the S3 service, create a bucket, and provide a bucket name. We’ve discussed this in detail here, so read that article first if you want to know more details.

- On the next dialog page, scroll down to the Default encryption option and tick on the Automatically encrypt objects option.

There are 2 options available here.
- AES-256 is the default server side encryption, where Amazon manages the entire key-creation process. It uses the 256-bit Advanced Encryption Standard to encrypt the data.

- AWS-KMS is the Amazon Key Management Service. This service provides easy management of all encryption keys used in Amazon. AWS-KMS can automatically assign keys or you can create your own. It uses FIPS 140-2 validated hardware security modules to isolate and protect keys. This is really strong protection, as FIPS 140-2 compliance is required by US military and government agencies.

- Confirm encryption options, either AES-256 or AWS-KMS on the next dialog page.


That’s it. From this point onward, data uploaded to this bucket will be automatically encrypted using the encryption service selected.